Accurate Inventory Data
Hardware attributes and installed software applications are automatically discovered by our reliable, lightweight client, delivering trustworthy details about each Windows, MacOS, ChromeOS, and Linux machine (including virtual and thin-client).
Essential Hardware Auditing
In addition to software product discovery and normalization, our client also records critical hardware information needed for lifecycle management and software deployment planning. With each login, computer details are updated, such as manufacturer, model, operating system version, CPU type and clock-speed, memory, disk size, free space, serial numbers, MAC address and more. Connected drives and monitors are also discovered automatically and added to device inventory.
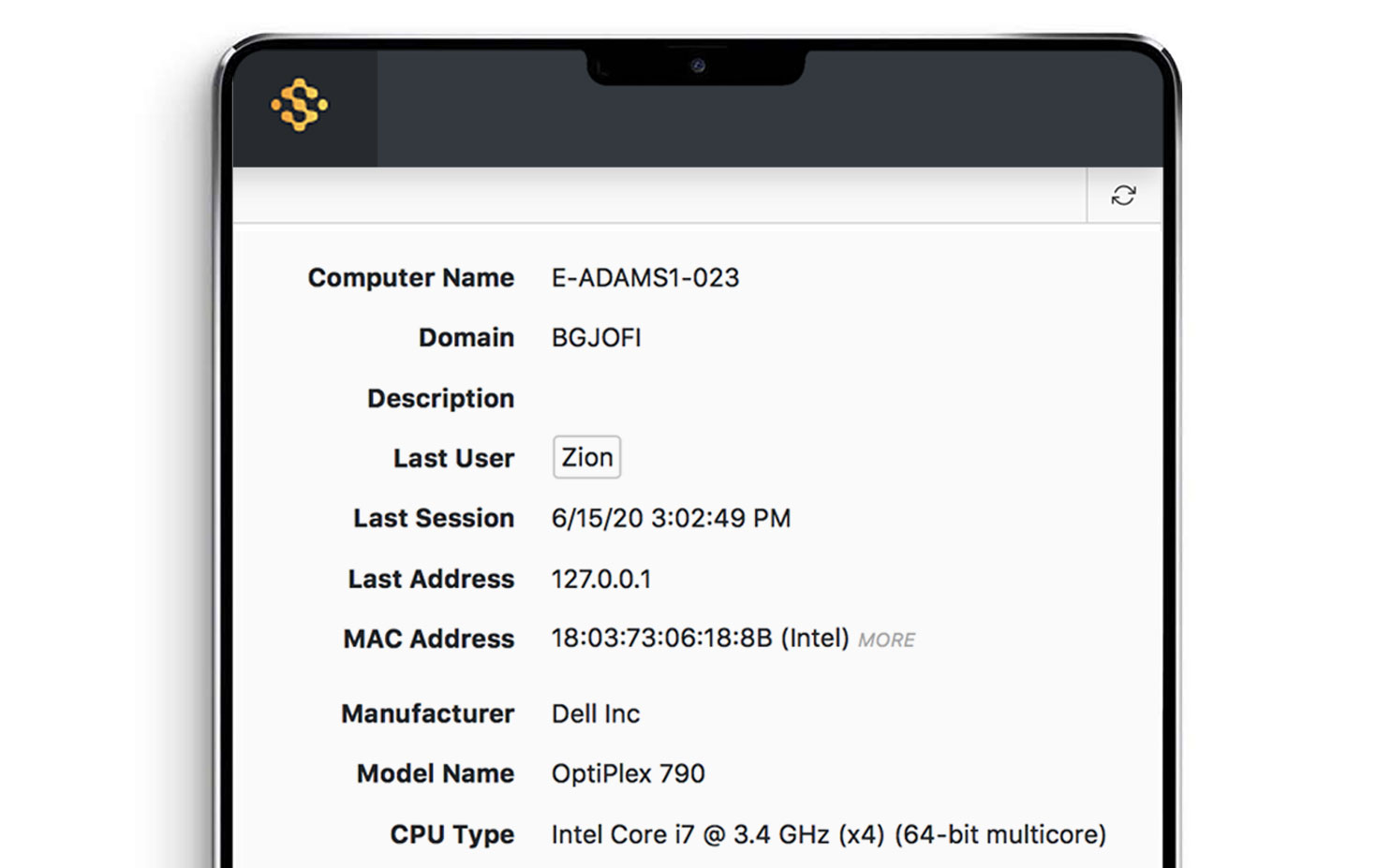
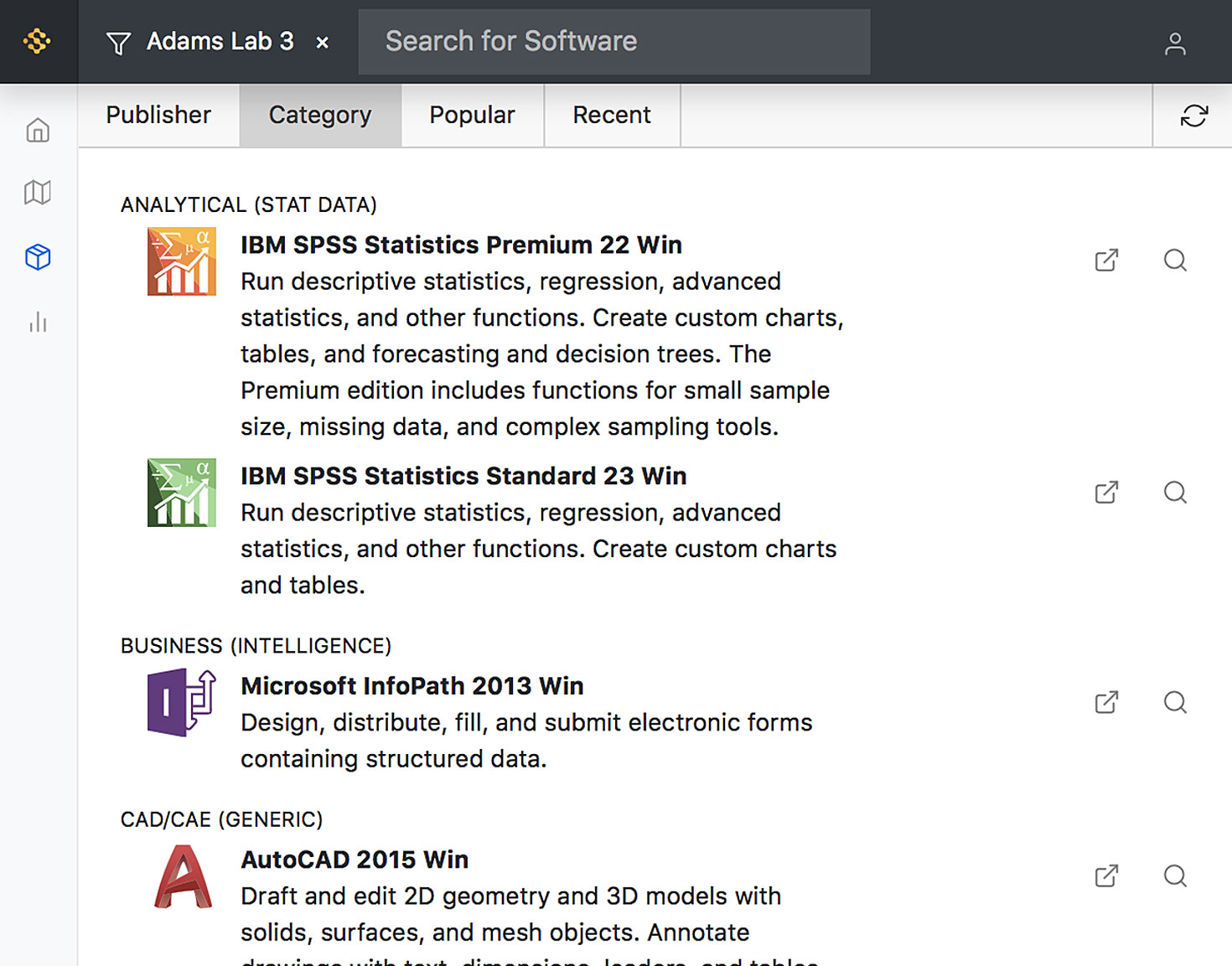
Software Product Recognition
After the initial program audit, our cloud-hosted Product Recognition Service (PRS) normalizes raw application data to determine exactly which software products and suites are installed on each computer. Product definitions are added and updated weekly, so you can always count on up-to-date details for virtually every product, and can even compare inventory baselines over time for a history of changes in software deployment.
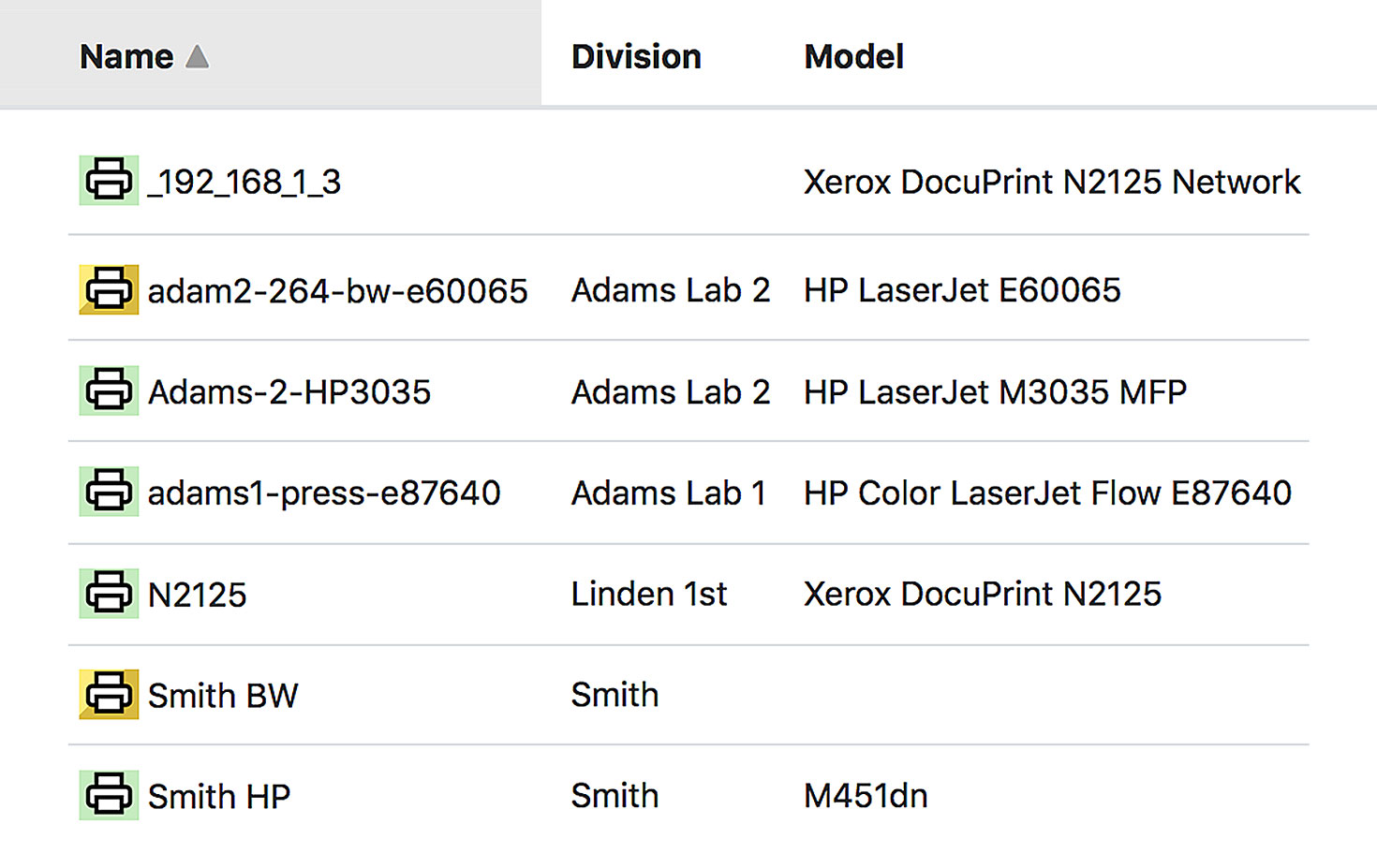
Printer Tracking
Import printers from a spreadsheet and establish a direct connection via IPP, or turn on our exclusive PaperCut integration for a completely automated printer database, including printer name, manufacturer, model, ink level, PPM, per page cost, and more.
Active Directory Integration
With Active Directory integration on, client computers automatically move into divisions matching your OU structure. Far from one-time OU mapping, Sassafras verifies the current location of every computer with each login, so you never have to worry about incomplete or inaccurate data, even after hardware redeployments.
Three Great Products to Select From
KeySight
LabSight
AllSight
Request a Demo
Contact us to see how these features will help you gain insight and reduce your IT Asset Management costs.